Besuchen Sie unseren neuen Webshop für weitere Produkte: stealth-phones.com
Besuchen Sie unseren deutschen Händler: https://www.anti-interception.com/
Mission und Vision
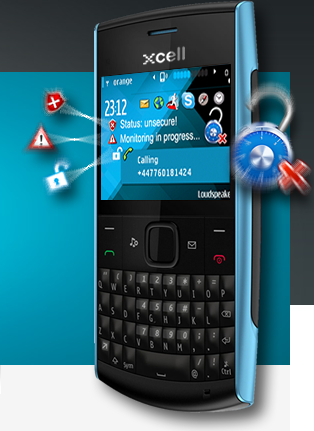
Security Begins with Intelligence. XCell. Powerful CounterIntelligence.
The confidentiality of private telephone calls has come under attack from many different angles. At risk are Governments, NGOs and PGOs, international organizations, executives as well as private individuals whose privacy is being threatened by increasingly sophisticated adversaries.
BETTER TO KNOW! Better to know when it happens than half way protection.
We often equate mobile security to physical security. A company hires a security guard, placing him at the front door of their building. The guard stands his post, checking ID's and ensuring the entrance safety. By standing at the front door he cannot ensure all company perimeter. He will have no clue about security breach, in case someone is simply jumping the fence and getting in.
Same when you use an encryption solution (software or hardware): you will never know when actually your cell phone is intercepted, and by consequence you will never know when you are in real danger.

Assuming that you are a target for an intelligence agency or any entity having enough financial resources to buy a GSM interceptor, have a guess on what they will do in case the you use an encrypted cell phone.
For sure they will use some other ways to get the info they need. They will not wait for some security flaws, they will not try to perform a deciphering attempt. They will simply bug your home, office and vehicle, will spy on your computer, will intercept your mail and will use covert human intelligence sources and whatever it takes to obtain relevant information about you and your activities. They can easily bypass the communication protection provided by the encrypted phones by simply collecting relevant informations from other sources. Simple as that.

On today market there are a variety of devices to encrypt your conversation. Though using of encryption to protect your privacy might be the prudent choice, the method has its own disadvantages:
A.You never know if encryption you use is indeed trustworthy and there is no reliable way to check it. Most of the encryption applications developers are not making public the source code. There can be (and most of the time there are) back doors used by law enforcement agencies.
Introducing a back door into a crypto system does not even require active cooperation of the manufacturer of the equipment. All it takes is one bribed programmer to compromise an entire product.
Some manufacturers of cryptographic equipment have a track record of hidden cooperation with intelligence agencies and interested private parties. Some of them are not even using publicly scrutinized and standardized crypto algorithms (like Diffie-Hellman, SHA256, AES and Twofish), but “proprietary” encryption methods that are not available for public evaluation. Several “proprietary” crypto-algorithms that were not subject to public review have been shown to be easily breakable in the past, like the COMP128 algorithm that is in use in many GSM networks for authentication, so the “proprietary crypto” approach has to be regarded as very risky.
B. Using of such devices might make you look suspicious and attract undesired attention to you.
C. If you are targeted by an intelligence agency, encrypting your mobile communications does not mean that you are 100% protected against eavesdropping. Think about that: will they drop you just because you use encrypted communication? No, for sure.. Being a challange for them, will find another ways to get the informations thet need. Sure, for a short period of time your secrets will remain... secret. But any decent agency will find at any time security breaches, gathering info they need about you, by any means.
Actually by encrypting your phone conversations, you are telling them that you have something important to hide and you force agencies to use other ways to gather intelligence.
D.An encrypted call is not so... encrypted, as you think. Even if you use a crypto phone, the GSM operator or the entity that operates a GSM interceptor can find out pretty much information such as:
- The phone number dialled by you or the phone number that is calling you. Hence, they can figure out the caller location and even his real identity. It is only a matter of time. They can (and they will do) tape his cell phone in order to find out who it is and what your relation with him is.
- The conversation length, time stamped.
- Your location at the moment of phone conversation.
- Your geographical location at every moment, by some simple and effective triangulation techniques.
Other crypto phone proven weaknesses:
- Some GSM interceptors can perform a DoS attack on your crypto phone, making that phone unavailable for use, for as long as they want. This occurs when crypto phone uses GPRS/data connection in order to transmit encrypted voice.
- Many modern GSM interceptors can downgrade your crypto phone connection from 3G to 2G, by simply jamming 3G uplink frequencies, which is a standard procedure. By doing that, many crypto phones that use data connections will fail and become useless.
- With carrier help, the phone IMEI can be blocked on the network.
- A GSM interceptor can perform a DoS attack on a BTS by continuously sending RACH bursts to all phones in the given area. This will affect all cell phones, including crypto phones from a certain area.
So, even if you use a crypto phone,there can be figured out the phone number and the person identity you are talking over the phone, your accurate locations, communication patterns etc. They will not know what you are talking about, but they will know when, for how long, where and who with. Sure, the voice call itself usually cannot be decrypted in a resonable period of time. But information above can be (and will be) used to find out in the end, your secrets.
That is why crypto phones can be used only for a short period of time as secure communication devices. In fact, being predictable is one of the worst choice on intelligence battlefield. And using a cryto phone means that you are more than predictable.
The only conclusion that you can make: instead of protecting your secretive communications in blind by using crypto phones, it is better to know when someone wants to find out your secrets and when they are trying to locate you. Then you can act advisedly, taking the right decisions and even influencing them by different deception techniques.
Do not assume that your secrets are hunted by various entities, all the time. This is not going to happen. Find out exactly when you are a target and for how long.

Better give them confidence by not using any encryption. Let them think that by intercepting your calls they can find out what they are looking for. Be smart and use to your advantage XCell Stealth phone: knowing if/when someone is tapping your cell phone, you can let them know what you want them to know about you. Smarter than encrypting your calls, in most cases. Only by using XCell Stealth phones you can be in control of your mobile communications and know about any interception attempts.
Security Begins with Intelligence. Xcell. Powerful CounterIntelligence
Unser Team
We are constantly looking for simple and innovative solutions with one thing in mind: mobile security. XCell Technologies is a dynamic company which seeks to enhance the protection of its customers by integrating a skilled, experienced and highly motivated team. Our mission is to provide our customer with the highest-quality services in intelligence and mobile security, turning our knowledge, expertise and passion into a value for their own benefit. Choosing XCell Technologies you will find a company that makes of excellence, innovation and non-conventional strategy its core philosophy.
The development staff consists of individuals spanning different languages, regions, industries, and nationalities. We are experts in offensive GSM security , cybercrime and security intelligence. We dedicate time and effort in ensuring that our product maintains its stature as the leader in the mobile security community.
It is fair to say that, with our background in signal intelligence and direct experience of working with GSM, XCell Stealth phones developers had a significant head start. And it is almost certainly this rare insight that guided us throughout our pragmatic approach to solving the problem at hand: alerting when your cell phone is being intercepted.

We are mobile/GSM security professionals, currently working with various Military and Government agencies and other clients who prefer to remain nameless. Our day-to-day work involves vulnerability research, cryptography, mobile remote exploitation, exploit development and Mobile Penetration Testing.
Creativity, skills and passion are the hallmarks of this close-knit group that faces every day with a positive attitude any new challenge.

Thanks to (in no particular order): Dieter Spaar, Harald Welte, David Burgess, Sylvain Munaut, James Moran (Fraud and Security Director GSMA Association), Dimitri Stolnikov, Chris Paget, Karsten Nohl, Collin Mulliner, Fabian van den Broek, Kurtis Heimer, Alexander Chemeris, Ivan Kluchnikov, Thomas Tsou, Ralph A. Schmid, Muhammad Junaid.
With the support of hackvision.de, osmocom.org and others who prefer to remain nameless, and all our friends and our advisory board.